- Administration
- Organization settings and permissions
- Set up single sign-on (SSO) with SafetyCulture
Set up single sign-on (SSO) with SafetyCulture
Learn how to set up single sign-on (SSO) for your SafetyCulture organization via the web app.Why set up single sign-on?
Single sign-on (SSO) is a great way to mitigate site access risks and reduce password fatigue from different username and password combinations. With SafetyCulture, you can set up SSO with any authentication solution that utilizes the Security Assertion Markup Language (SAML) 2.0 standard. This includes some of the most common solutions such as Active Directory (ADFS, Azure), PingFederate, Google, and Okta.
Please note that our customer support team can only provide limited help for single sign-on, user provisioning, and integrations via third-party platforms such as Power Automate, Power BI, and Zapier. If your organization is on the Enterprise Plan, please contact your customer success manager for assistance.
How do I get started with single sign-on?
You just need to make sure your organization is on the Premium Plan or Enterprise Plan and that your single sign-on solution utilizes the Security Assertion Markup Language (SAML) 2.0 standard. If you're not sure, you can confirm with your IT team.
If your organization uses Azure Active Directory for single sign-on, and you want to set up JIT user provisioning, you can also refer to Microsoft's support article for instructions.
Please note that the Microsoft Gallery app currently doesn't support SCIM user provisioning.
What you'll need
Single sign-on solution that utilizes SAML 2.0
Single sign-on connections are organization-specific. If you’re a part of multiple organizations and want to set up a single SSO connection for all your organizations, please contact your Customer Success Manager for assistance.
Single sign-on options
You can set up either SAML or ADFS SSO with one of the following options:
Service Provider (SP)-initiated SSO (recommended): A user that tries to log in via SafetyCulture will be automatically redirected to your company's SSO portal for authentication. A successful authentication will automatically redirect the user back to SafetyCulture.
Identity Provider (IdP)-initiated SSO: A user that tries to log in via SafetyCulture must start from your company's SSO portal for authentication. A successful authentication will take the user to SafetyCulture.
Set up single sign-on (SSO)
Click your organization name on the lower-left corner of the page and select Organization settings.
Select Security on the top of the page.
Click Set up in the "Single sign-on (SSO)" section.
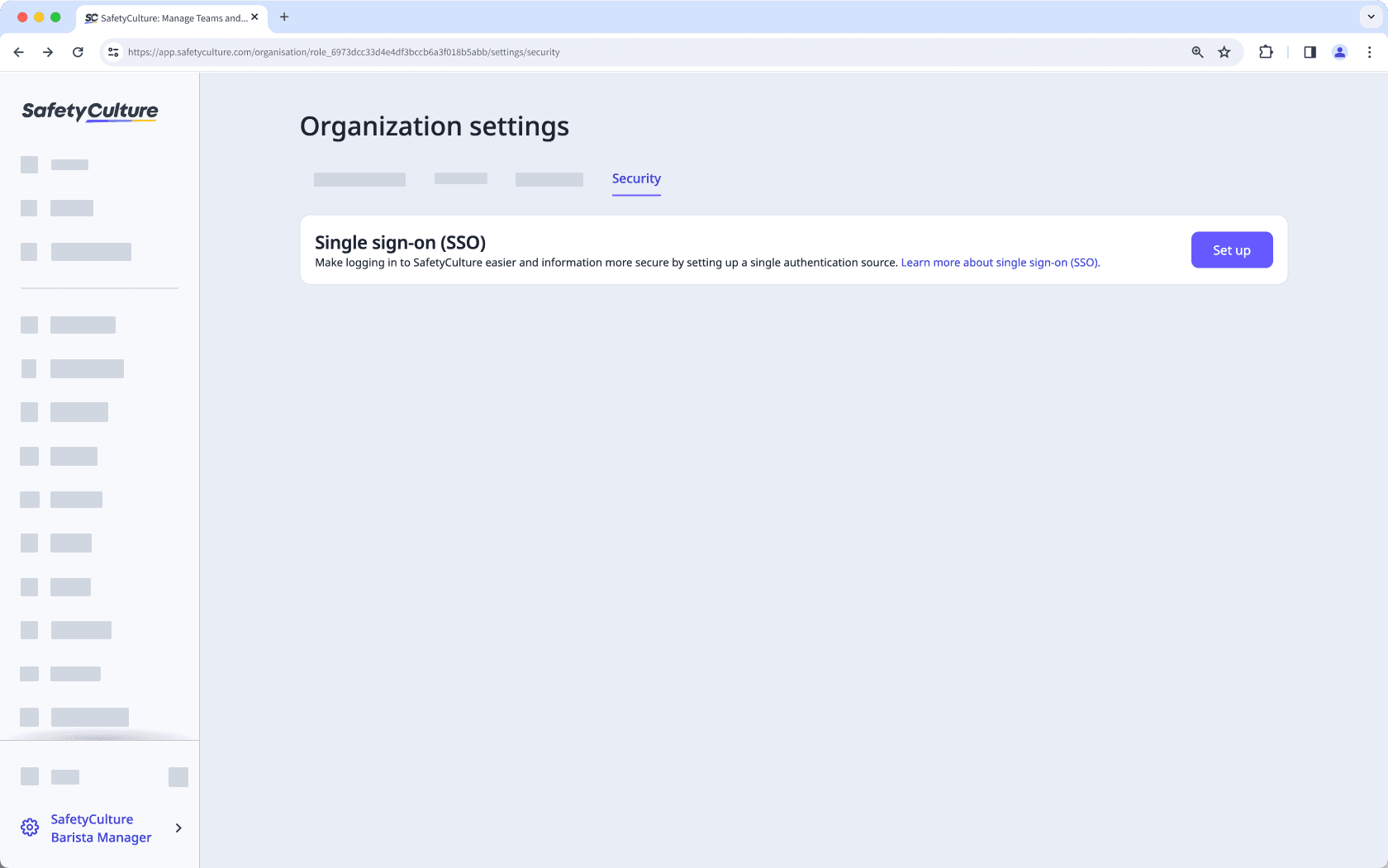
Select which SSO connection you want to use and configure your connection accordingly.
Click Complete setup.
Click Close.
Configure Generic SAML
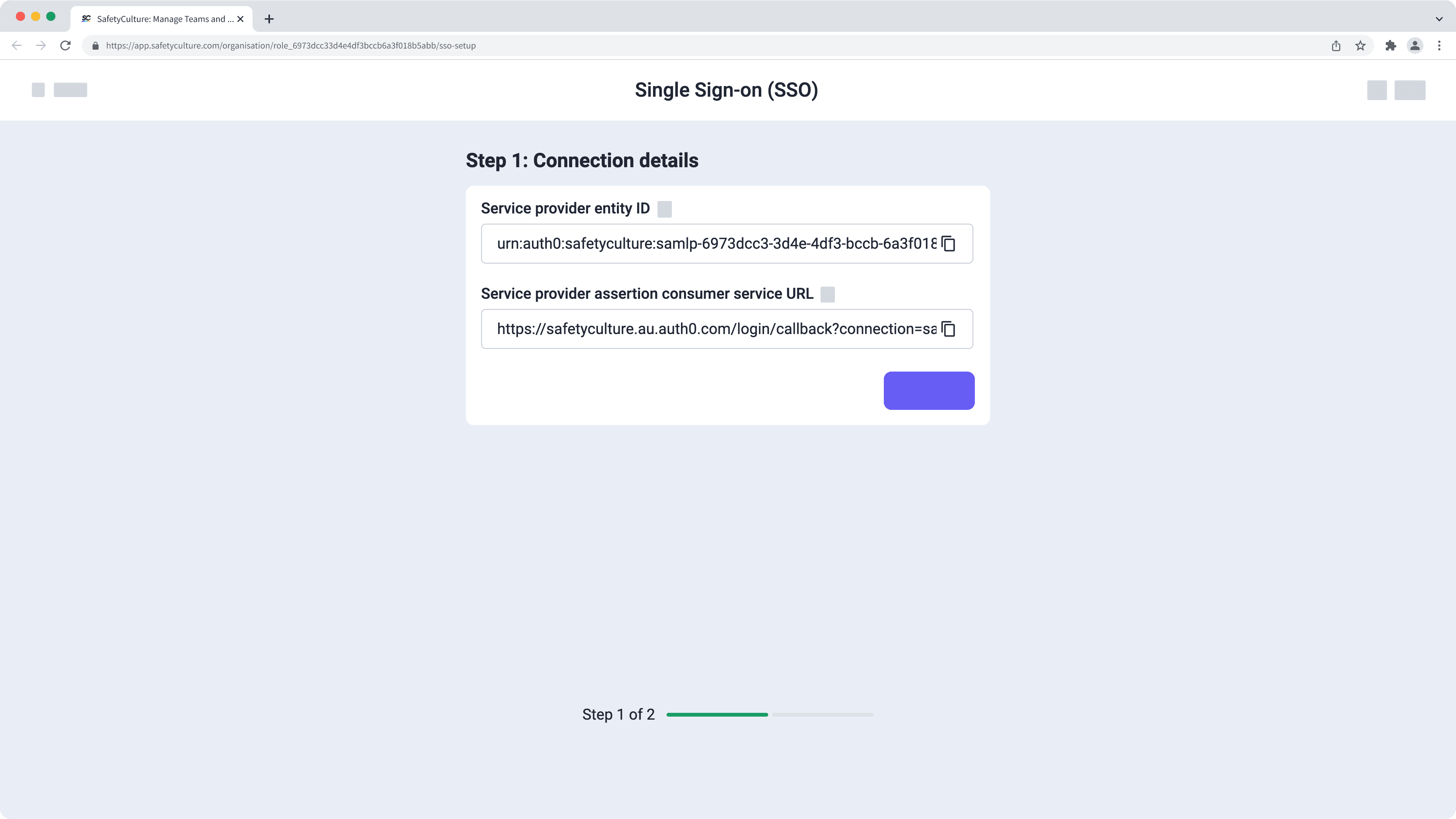
SafetyCulture uses Auth0 as the SSO broker, which requires the following settings:
Assertion-consumer Service URL (Application Callback URL)
Entity ID (Audience)
This information is provided during the SSO setup process within the SafetyCulture web app. If the Identity Provider offers a choice for bindings, you should select "HTTP-Redirect" for the authentication request.
Active Directory Federation Services (ADFS)
Active Directory Federation Services (ADFS) is a commonly used SSO solution that's created by Microsoft. ADFS manages authentication through a proxy service, hosted between a company's Active Directory and SafetyCulture.
ADFS Web Services Federation
Follow the instructions to connect SafetyCulture as an app to ADFS and apply the following settings where required:
Realm Identifier:
urn:auth0:safetycultureRelying Party Trust identifier:
urn:auth0:safetycultureEndpoint:
https://safetyculture.au.auth0.com/login/callback
ADFS SAML WebSSO
Follow the instructions to add SafetyCulture as a relying party and apply the following settings where required.
Display Name:
urn:auth0:safetyculture.au.auth0.comRelying party trust identifier:
urn:auth0:safetyculture.au.auth0.comPost-back URL:
https://safetyculture.au.auth0.com/login/callback?connection={name_provided_in_app}Entity ID:
urn:auth0:safetyculture
Frequently asked questions
Yes, you can restrict your organization's users to logging in via your SSO provider by setting your SSO login type to "Allow SSO login only".
Yes, you can do so by updating your organization's SSO login type setting to "Enforce SSO for named domains". Once selected, the setting will enforce SSO login based on a user's account email.
If a user's email domain matches the ones configured for their organization's SSO connection, they can only log in using their SSO account.
If a user's email domain doesn't match the ones configured for their organization's SSO connection, they can log in using their password and still have the option of using their SSO account if it applies to them.
It's likely that you haven't set the "email" attribute or claim in your SAML responses. Please check if you have an attribute called "email" in your SAML responses. If the email in the response isn't called "email", please rename the field to "email".
If the above steps still don't resolve the problem, please reach out to your point of contact from SafetyCulture for assistance.
Once the single sign-on for your organization is set up successfully, you can enable IdP-initiated login via the web app:
Click your organization name on the lower-left corner of the page and select Organization settings.
Select Security on the top of the page.
Click
Edit in the "Single sign-on (SSO)" box.
Turn IdP initiated login on.
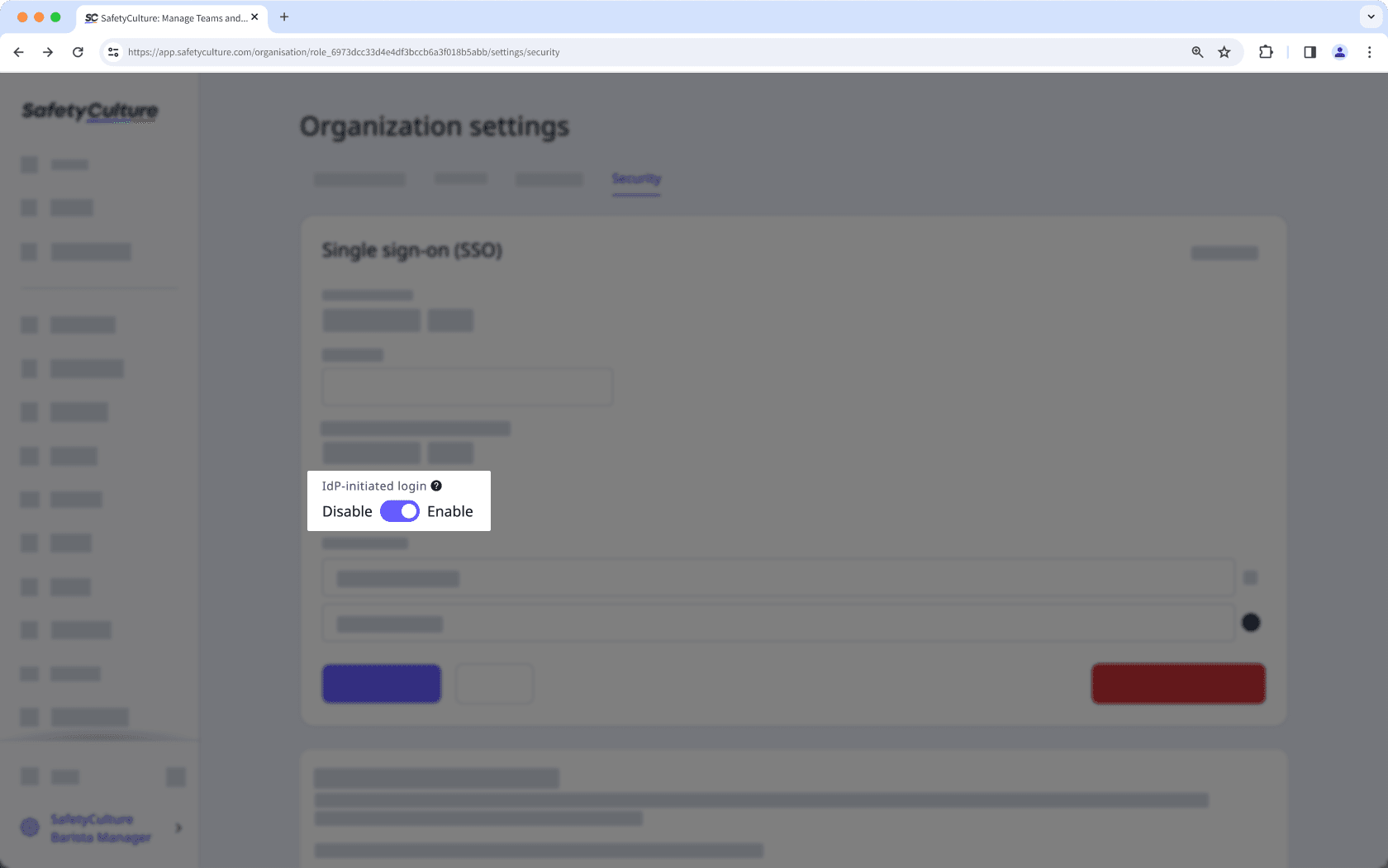
Click Save changes.
Please reach out to your point of contact from SafetyCulture for assistance.
No, you don't need to verify the email domains for your organization's SSO to work. However, if you want to use just-in-time (JIT) provisioning for your organization, you'll need to verify the email domains.
To update your SSO connection, you would need to delete it and then set it up again with the updated information:
Click your organization name on the lower-left corner of the page and select Organization settings.
Select Security on the top of the page.
In the "Single sign-on (SSO)" section, click
Edit.
Click Delete SSO connection.
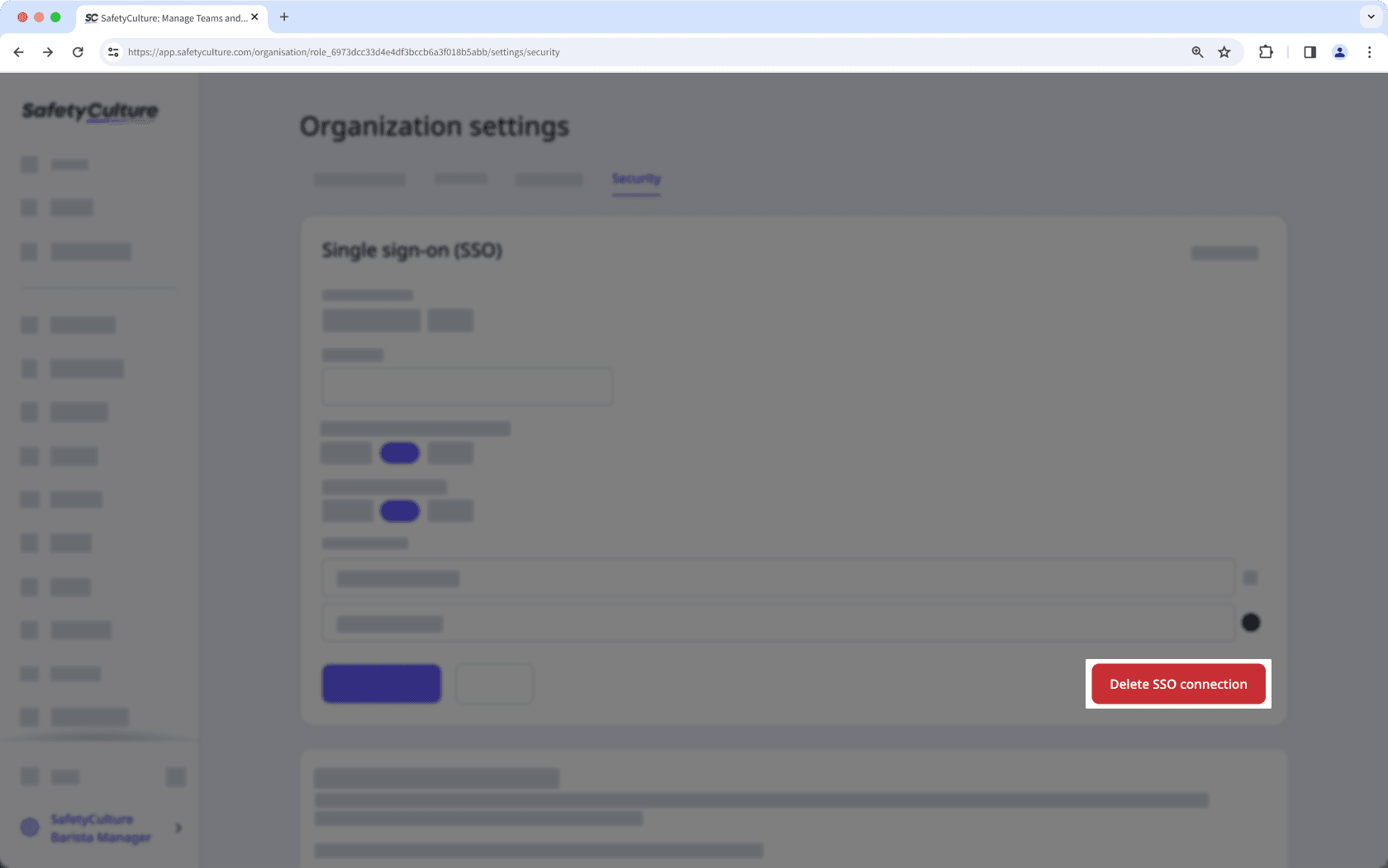
In the pop-up window, click Delete.
Was this page helpful?
Thank you for letting us know.